Quishing, or QR code phishing, is a type of social engineering attack that leverages QR codes to mislead users into visiting malicious websites.
Humans remain the weakest element in any cyber defense strategy. Regardless of the types and number of installed security solutions, organizations continue to fall victim to cyberattacks because of mistakes caused by their employees.
Social engineering (SE) attacks remain the preferred method threat actors use to circumvent the technical securities placed and infiltrate target organizations' IT environments. A study conducted by PurpleSec using stats from various sources found that 98% of cyberattacks rely on some form of social engineering to gain an entry point into target IT systems. The FBI's 2023 IC3 Report found that phishing/spoofing — which is the most common type of SE attack — was the most used medium to execute cyberattacks against US companies in 2023.
There are different forms of SE attacks; some could be executed online (via the internet), others by phone or text messaging, and others offline (via physical objects such as paper posters or malicious QR codes).
In this article, I will discuss a specific form of phishing that could be delivered online or offline. This type is called quishing, and it has been gaining more attention lately because few internet users are aware of it and its potential risks.
What is quishing?
Quishing, also known as QR Code phishing, is a type of SE attack that leverages QR codes to mislead unsuspecting users into visiting malicious websites to execute further attacks against them, such as stealing sensitive information or installing malware.
How is a quishing attack performed?
Quishing works similarly to traditional phishing attacks, where the URL to the malicious website is delivered via email or SMS messages. However, in quishing, the QR code is decoded into a URL that points to the malicious website. The malicious QR code can be printed on paper or simply created digitally on digital posters and delivered via social media posts or emails.
In general, all quishing attacks follow these general steps:
- Threat actors create malicious QR codes that redirect to their malicious websites.
- Threat actors spread these QR codes in different places, such as printing the QR code on a piece of paper and placing it in a parking area or a hotel lobby (see Figure 1, source), announcing it as a free WiFi connection, for example.
- Unaware users scan the QR code using their smartphone camera, and their web browser is directed to the malicious website or prompted to install a malicious application containing malware (e.g., keylogger, ransomware).
- After visiting the malicious destination, the unaware user may be prompted to:
- Enter their sensitive information into the website form, such as login credentials for their online accounts (social media platforms; financial information such as banking or credit card details; email; or online merchants).
- Install an application containing malware to spy on their device or gain remote control over
- Participate in a large botnet to execute a distributed denial of service attack (DDoS) against a specific target.
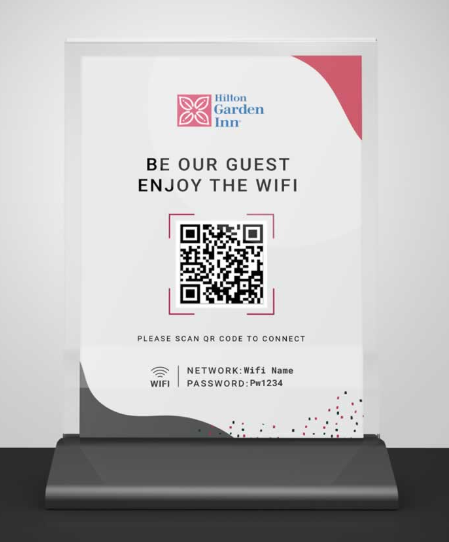
Figure 1 - Sample WiFi QR code flyer that could be abused for malicious purposes
Quishing attack scenarios
QR codes are increasingly used to streamline users' experiences in public places when accessing online content in addition to other use cases. For example, QR code technology is widely used in:
- Restaurants, hotels, education centers, hospitals and other public places to allow visitors to access their free WiFi internet
- Companies to lead customers to their website landing pages
- Restaurants menus so customers can browse and order food
- Application stores, such as Google Play and Apple Store, for applications in their stores; unique QR codes allow application owners to spread their apps both online and offline
- Location data storage; for example, a shop prints its location data into a QR code card and distributes it online and offline to customers. QR Code Generator for Google Maps allows storing Google Map URLs in a QR code.
- Social profiles to facilitate sharing of users' social media profiles; here are two free services for generating QR codes: QR code Generator and Adobe free online QR Code generator
- Product and service payment; you can access the online payment portal to pay fees by scanning the QR code of the merchant
These were some use cases of QR codes. Here are some examples of how threat actors may use quishing to mislead unaware internet users to malicious websites:
Malicious QR codes in public places
Threat actors may create fake QR codes and place them in public areas, such as restaurants, airports, shopping malls, or bus stations, claiming to provide free WiFi access, discounts on buying a product/service or other incentives. When unsuspecting people scan these QR codes, they are redirected to malicious websites designed to steal their personal information or to infect their computing devices with malware.
A real-world example of such an attack tactic is what happened with a woman in Singapore last year. The woman visited a bubble tea shop and saw a sticker pasted on its glass door. The sticker encouraged customers to complete an online survey to win a prize, which was a free cup of milk tea. The woman scanned the QR code on the sticker and downloaded an application into her Android phone. The app was malicious and allowed attackers to control her device, access her banking account information and steal $2,0000.
QR codes sent via phishing emails or SMS messages
Threat actors may send phishing emails or text messages containing QR codes that appear to be from legitimate sources, such as banks, medical health providers, online merchants, delivery services or government agencies. When scanned, the QR codes will lead users to the attackers' websites that mimic the appearance of a legitimate organization. The aim here is to steal sensitive information or download malware.
Malicious QR codes on product labels
Threat actors may create advertisements for some products with embedded QR codes that appear to provide detailed information about the product. However, when scanned, these QR codes direct users to malicious websites.
QR code hijacking
Attackers may hijack legitimate QR codes by overlaying them with malicious ones or replacing the original code with a malicious version. This can occur on websites, printed materials or other physical objects. When victims scan the hijacked QR code, they are redirected to a malicious website controlled by the attacker.
How to prevent quishing attacks
To prevent quishing attacks, we should follow the following practices:
- Quishing could be delivered via emails, social media posts and other digital mediums. When receiving an email containing a QR code that needs to be scanned, make sure to check the email for phishing signs (e.g., grammatical errors, misspellings impersonating a legitimate domain name to hide the actual sender) and use a sense of urgency to act promptly.
- Verify the QR code before visiting the URL behind it. This could be achieved using a secure QR code reader, such as the Trend Micro™ QR Scanner (Android) and QRs (Apple devices). You can also decode the URL behind the QR code by using free online services like ZXing Decoder Online or QR Code Scanner (see Figure 2).
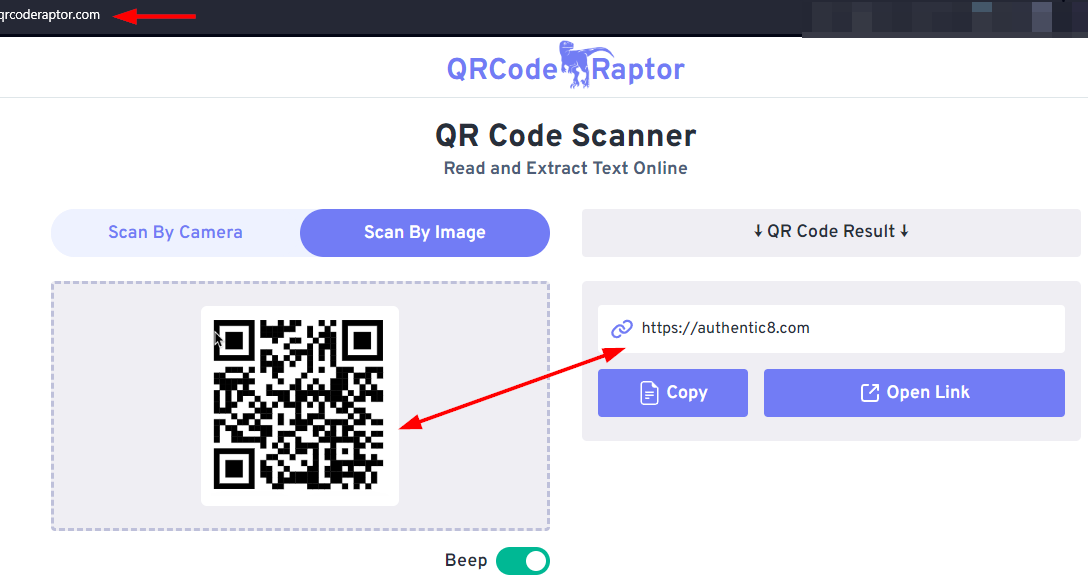
Figure 2 - Using qrcoderaptor.com, a free online service to decode QR Codes
Learn more about using OSINT to investigate phishing websites >
Installing a secure QR code reader on your smartphone will help you reveal any QR code you may encounter in public places easily. Online services are also helpful in revealing the actual URL of QR codes when received in digital formats.
- Always be suspicious when visiting a website via QR code scanning. When accessing your important online accounts, such as banking or medical accounts, it is always advisable to type the website address directly in the web address bar and avoid using the QR code scanning method.
- When downloading applications using QR codes, make sure to verify the destination URL first and ensure it is from a legitimate and trusted source.
- If you are reading a QR code printed on a sticker or physical surface, carefully inspect for signs of tampering. Threat actors may attempt to overlay their malicious QR codes on top of legitimate ones.
- Exercise caution and do not unquestioningly trust QR codes found in public places. If there is a need to use a QR code in such locations, make sure to reveal its true destination using a reliable QR code reader or online service.
- Keep your operating system and installed applications current. Install an antivirus program on your device and ensure your device has the latest security patches installed.
As general advice, be wary of unsolicited emails, SMS messages or social media messages containing QR codes, even if they appear to be from legitimate sources. Always verify the QR code before visiting the QR-decoded website.
Get more helpful tips on threat intelligence in this guide >


